Implement LDAP authentication in Tomcat & JBoss server for Java app
In this article we will explore the ways to implementation of LDAP (Lightweight Directory Access Protocol) authentication in Tomcat as well as JBoss server. First let us see briefly what LDAP is.
Introduction to LDAP
Following is what Wikipedia has to say about LDAP: The Lightweight Directory Access Protocol, or LDAP is an application protocol for querying and modifying directory services running over TCP/IP. A directory is a set of objects with similar attributes organized in a logical and hierarchical manner. The most common example is the telephone directory, which consists of a series of names (either of persons or organizations) organized alphabetically, with each name having an address and phone number attached. An LDAP directory tree often reflects various political, geographic, and/or organizational boundaries, depending on the model chosen. LDAP deployments today tend to use Domain name system (DNS) names for structuring the topmost levels of the hierarchy. Deeper inside the directory might appear entries representing people, organizational units, printers, documents, groups of people or anything else that represents a given tree entry (or multiple entries).Configurations in Tomcat Server
I assume you have installed JDK and Tomcat server and have set few environment variables such as CLASSPATH, PATH, JAVA_HOME, CATALINA_HOME etc. First step is to implement LDAP in Tomcat is to modify server.xml. Open server.xml from conf directory from your Tomcat installation directory and add following tag between tag <Host> and </Host>.<Realm className="org.apache.catalina.realm.JNDIRealm"
debug="99"
connectionURL="ldap://ldap.viralpatel.net:389/"
userPattern="{0}" />
Code language: HTML, XML (xml)<!—
<Realm className="org.apache.catalina.realm.UserDatabaseRealm"
debug="0"
resourceName="UserDatabase"/>
-->
Code language: HTML, XML (xml)- className: This is the fully qualified Java class name of this Realm implementation. The value “org.apache.catalina.realm.JNDIRealm” must be specified here.
- debug: This is the level of debugging detail logged by this Realm to the associated log file. Higher numbers generate more detailed output. If not specified, the default debugging detail level is zero (0).
- connectionURL : This is a URL whose format is defined by the JNDI provider. It is usually an LDAP URL that specifies the domain name of the directory server to connect to, and optionally the port number and distinguished name (DN) of the required root naming context. Often the distinguished name of the user’s entry contains the username presented for authentication but is otherwise the same for all users. Here, the phrase “ldap://ldap.viralpatel.net:389/”, “ldap” represents a protocol; “ldap.viralpatel.net” represents a LDAP directory server to connect; “389” represents a valid port on the server.
- userPattern : This is used to specify the DN, with “{0}” marking where the username should be substituted.
<security-constraint>
<web-resource-collection>
<web-resource-name>Logging Area</web-resource-name>
<description>
Authentication for registered users.
</description>
<url-pattern>/*</url-pattern>
<http-method>GET</http-method>
<http-method>POST</http-method>
</web-resource-collection>
<auth-constraint>
<role-name>*</role-name>
</auth-constraint>
</security-constraint>
<security-role>
<role-name>*</role-name>
</security-role>
<login-config>
<auth-method>BASIC</auth-method>
<realm-name>Please enter your Username</realm-name>
</login-config>
Code language: HTML, XML (xml)<!—restricted files under folder “Admin”
<url-pattern>/Admin/*</url-pattern>
<!—restricted file OfficeDocIndex.jsp
[/code]
To fetch the user details in Java, copy following code in your JSP/Java file.
[code="java"]
import java.security.Principal;
……
Principal principal = request.getUserPrincipal();
String userName = principal.getName();
.…
[/code]
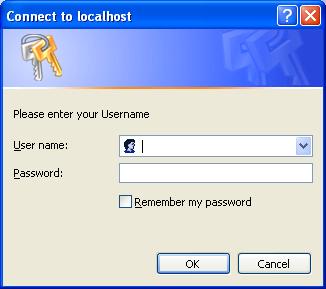
Now once you start the Tomcat and visit your website, following popup will be shown.
<img src="//www.viralpatel.net/app/uploads/2008/12/ldap-authentication-popup-tomcat-server.jpg" alt="ldap-authentication-popup-tomcat-server" title="ldap-authentication-popup-tomcat-server" width="326" height="289" class="alignnone size-full wp-image-394" />
<h2>Configurations in JBoss Server</h2>
I assume you have installed JDK and JBoss server and have set few environment variables such as CLASSPATH, PATH, JAVA_HOME etc.
First step is to implement LDAP in JBoss is to modify <strong>login-config.xml</strong>. Open login-config.xml from <strong>conf </strong>directory from your JBoss installation directory and add following tag.
<!-- wp:code {"language": "xml"} --><pre class="wp-block-code"><code></code></pre><!-- /wp:code -->
<application-policy name="website-domain">
<authentication>
<login-module code="org.jboss.security.auth.spi.LdapLoginModule" flag="required">
<module-option name = "debug">true</module-option>
<module-option name = "java.naming.factory.initial">
com.sun.jndi.ldap.LdapCtxFactory
</module-option>
<module-option name = "java.naming.provider.url">
ldap://ldap.viralpatel.net:389/</module-option>
</login-module>
</authentication>
</application-policy>
Code language: HTML, XML (xml)<?xml version="1.0" encoding="UTF-8"?>
<jboss-web>
<security-domain>java:/jaas/website-domain</security-domain>
</jboss-web>
Code language: HTML, XML (xml)<security-constraint>
<web-resource-collection>
<web-resource-name>ADMIN</web-resource-name>
<description>An example security config that only allows users with the
role ADMIN to access the HTTP servlets
</description>
<url-pattern>/*</url-pattern>
<http-method>GET</http-method>
<http-method>POST</http-method>
</web-resource-collection>
<auth-constraint>
<role-name>*</role-name>
</auth-constraint>
</security-constraint>
<login-config>
<auth-method>BASIC</auth-method>
<realm-name>Authentication require</realm-name>
</login-config>
<security-role>
<role-name>*</role-name>
</security-role>
Code language: HTML, XML (xml)import java.security.Principal;
// Get principal from the request.
Principal principal = request.getUserPrincipal();
String userName = principal.getName();
// deal with the userName get from principal.
Code language: Java (java)Recent Posts
- Java
Java URL Encoder/Decoder Example
Java URL Encoder/Decoder Example - In this tutorial we will see how to URL encode/decode…
5 years ago
- General
How to Show Multiple Examples in OpenAPI Spec
Show Multiple Examples in OpenAPI - OpenAPI (aka Swagger) Specifications has become a defecto standard…
5 years ago
- General
How to Run Local WordPress using Docker
Local WordPress using Docker - Running a local WordPress development environment is crucial for testing…
5 years ago
- Java
Create and Validate JWT Token in Java using JJWT
1. JWT Token Overview JSON Web Token (JWT) is an open standard defines a compact…
5 years ago
- Spring Boot
Spring Boot GraphQL Subscription Realtime API
GraphQL Subscription provides a great way of building real-time API. In this tutorial we will…
5 years ago
- Spring Boot
Spring Boot DynamoDB Integration Test using Testcontainers
1. Overview Spring Boot Webflux DynamoDB Integration tests - In this tutorial we will see…
5 years ago

View Comments
So interesting! I couldn't even guess it might be so exciting!
You can use request.getRemoteUser() instead.
Hi,
One question: what should be the LDAP "structure" for the logins to succeed?
I mean, how can I tell what DN to use, how to find users, and where are the roles defined in LDAP?
I can have for example a DN like this:
uid=jack, ou=people, dc=example, dc=com
So the user will have attributes in LDAP, the password for example, and the roles ... where in LDAP will I define user roles so that JBoss will pick them from the correct attribute?
Thanks
Hi Viral,
Thanks for such a wonderful site.
I tried to implement this, but i had no success.
The authentication window pops up but when i give uid and pwd it doesnot take it.
After 3 attempts i get 404 error.
1. I updated server.xml
2.Update web.xml
3 .Added jars to commons/lib directory too.
Thanks,
Naveen.
Hi
This Tutorial is incomplete and does not help,
Why is it inclomplete what is missing. plz give us details
Viral,
is the info for implementing ldap still valid for JBOSS AS 7
@rd I did not find any login-config.xml in JBoss 7. So I am not sure if this tutorial is applicable for AS 7.
hi i am trying to integrate jack rabbit to the jboss .. if u have any idea just post it.... and mail me also.... and i forgot to tell something ur post s are very help full to me at the time of need
I am new to LDAP , please explain me in detail, how roles are defined in this concept, and we have to use only jboss ? no other servers we have to use please answer this
Hi Viral,
Have implemented the same in apache successfully. Tested too. But how the same can be done for Websphere 7?
Can you please tell us in detail?
Thanks !!!
Hi Tilak,
can you please mail me the procedure how did you implement the above code in the apache successfully.
waiting for your reply.
T&R,
Khaleed K