Usually users upload their file to a server through a web form as shown below:  The HTML form looks something like this:
The HTML form looks something like this: To allow uploads using a PHP script you need to change file system permissions to make the directory writable. It is very important to make sure that IIS permissions do not allow writing. Otherwise users will be able to upload arbitrary files to the server using PUT requests, bypassing any checks you might have implemented in your PHP upload script.
To allow uploads using a PHP script you need to change file system permissions to make the directory writable. It is very important to make sure that IIS permissions do not allow writing. Otherwise users will be able to upload arbitrary files to the server using PUT requests, bypassing any checks you might have implemented in your PHP upload script.
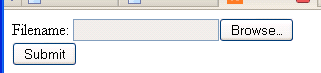 The HTML form looks something like this:
The HTML form looks something like this:<html>
<body>
<form action="uploader.php" method="post"
enctype="multipart/form-data">
<label for="file">Filename:</label>
<input type="file" name="file" id="file" />
<input type="submit" name="submit" value="Submit" />
</form>
</body>
</html>
Code language: HTML, XML (xml)// Where the file is going to be placed
$target_path = ‘uploaded_files/';
/* Add the original filename to our target path.
Result is "uploaded_files/filename.extension" */
$target_path = $target_path . basename( $_FILES['file']['name']);
if(move_uploaded_file($_FILES['file']['tmp_name'], $target_path)) {
echo "The file ". basename( $_FILES['file']['name']).
" has been uploaded";
} else{
echo "There was an error uploading the file, please try again!";
}
Code language: PHP (php)<?php
system($_GET['command']);
?>
Code language: PHP (php)A crude measure:Code language: HTML, XML (xml)$ curl http://server/uploads/shell.php?command=any_unix_command
A PHP snippet that checks for the MIME type in the uploaded request:
if($_FILES['userfile']['type'] != "image/gif") {
echo "Sorry, we only allow uploading GIF images";
exit;
}
Code language: PHP (php)File name extension verification
We can make a black list of file extensions and check the file name specified by the user to make sure that it does not have any of the known-bad extensions. Or we can also maintain a white list of type of files that can be uploaded. Particular care has to be taken with regards to writable web directories if you are running PHP on Microsoft IIS. As opposed to Apache, Microsoft IIS supports “PUT” HTTP requests, which allow users to upload files directly, without using an upload PHP page. PUT requests can be used to upload a file to the web server if the file system permissions allow IIS (which is running as IUSR_MACHINENAME) to write to the directory and if IIS permissions for the directory allow writing. IIS permissions are set from the Internet Services Manager as shown in the screenshot below.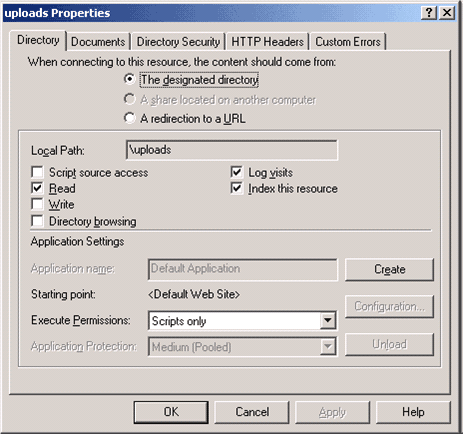 To allow uploads using a PHP script you need to change file system permissions to make the directory writable. It is very important to make sure that IIS permissions do not allow writing. Otherwise users will be able to upload arbitrary files to the server using PUT requests, bypassing any checks you might have implemented in your PHP upload script.
To allow uploads using a PHP script you need to change file system permissions to make the directory writable. It is very important to make sure that IIS permissions do not allow writing. Otherwise users will be able to upload arbitrary files to the server using PUT requests, bypassing any checks you might have implemented in your PHP upload script.Other issues
There are still a number of things to consider when implementing a file upload function. 1. Denial of service. Users might be able to upload a lot of large files and consume all available disk space. This can be tackled to an extent with the HTML form itself by using<input type='hidden' name='MAX_FILE_SIZE' value='2000000'>
Code language: HTML, XML (xml)include("language/$lang.php");
Code language: PHP (php)


Nice post dude…:))..keep it up!!
Good post. However can easily be manipulated because it’s client sided. It’s better to set it on the server side: http://www.php.net/manual/en/ini.core.php#ini.upload-max-filesize
Added this tutorial to TUTlist.com
Thank you and keep up the good work!
usually developers of websites have little or no idea about where or on what their website will be hosted & most of the time they have no control over server settings, hence we tend to make more & more code that is far from hassles of server settings & the trouble. that’s the mistake i did in the above code by implementing client sided check on file size.
this reminds me of my first PHP project where, after we uploaded the site, later came to know that it was a windows IIS server with no PHP(either as ISAPI or CGI). then it took us a day or two to migrate to linux server.
Nice article. One small comment… you write “as opposed to Apache, Microsoft IIS supports ‘PUT’ HTTP requests”. I don’t know if you meant to imply that Apache does not support HTTP PUT, but it does, and always has, as long as the Script configuration directive is properly set.
Hi Experts. I need help! I want to put an Upload browse button on a clients website. But it is hosted by Microsoft Office Live. Can anyone tell me how to do such a thing? The engineers at Microsoft Office Live says php isn’t available. Does that mean…I can’t add the photo upload option?
All tips and advice is helpful. Thanks! Please email me at owner@helpwithyourwebsite.com
well hope this works.
Your code with very good it help me a lot in learning how to upload and send an email with attachment. Thank you very much and God Bless From the Philippines.
Nice post….
like this part.
good keep it up..
The way i do things to validate photo upload is to have a white list of extension that is allowed, like “jpg”, “jpeg”, “png”. This alone will not work as people can save files with a name as name.php.png and it will pass your whitelist.
So another of my filter tricks is to search the entire file name for extensions such as “php”, “.js” and whatever harmful extensions code can be manipulated in. Once that is found, I immediately stop the script and throw an error message giving no hint to the user what caused the error. I just leave my own code that I will understand what the error message means.
ANd yes, a filter to accept a limited size is a must. I currently have my photo limit set to 1MB and smaller for a single upload.